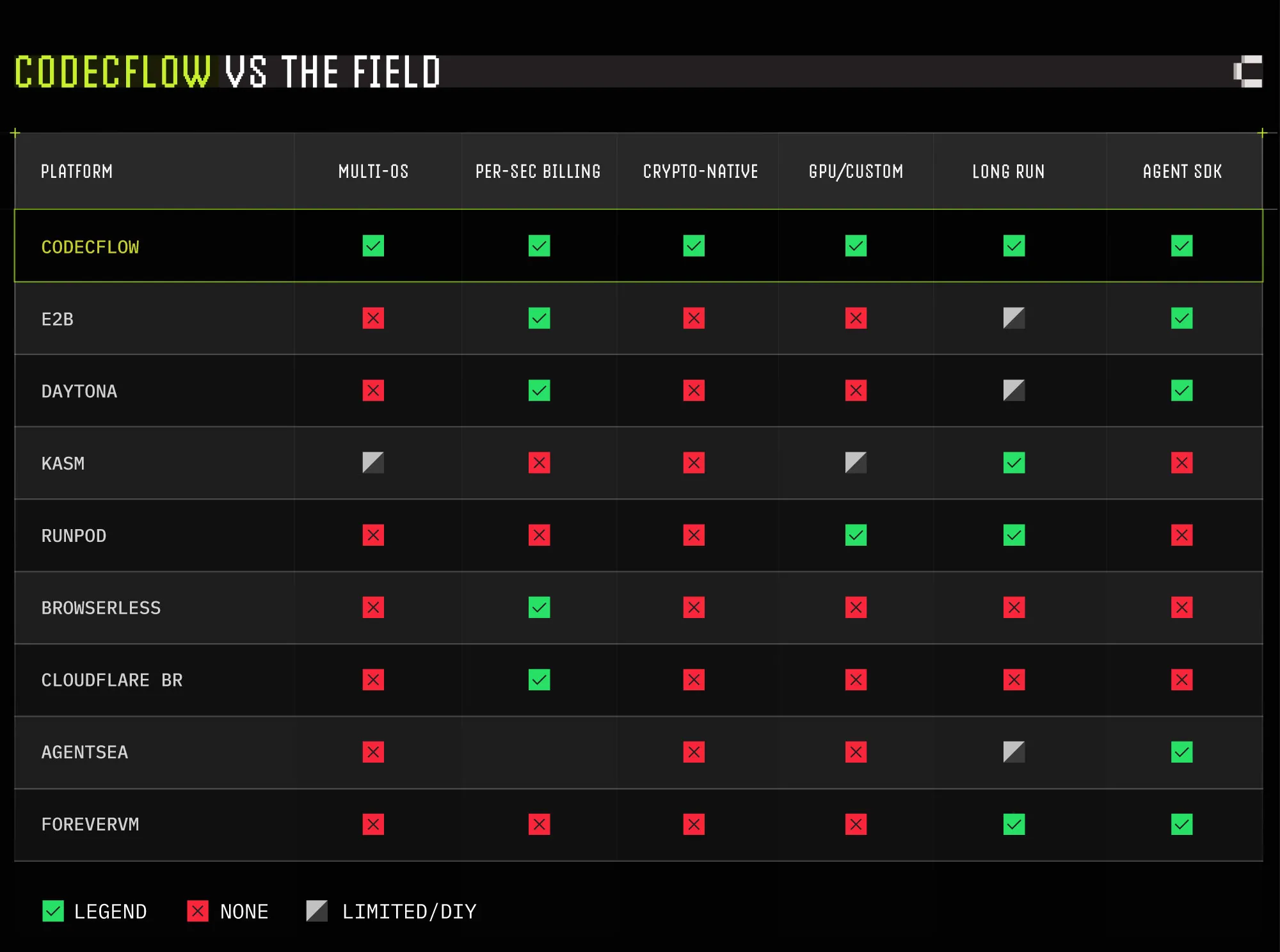
Machine: Compute Infrastructure
Fabric Orchestration
Section titled “Fabric Orchestration”The platform automatically provisions dedicated compute “machines” for each Operator, avoiding complex multi-node clusters. Instead of multiple agents sharing one cluster, each Operator gets its own isolated VM or container instance. This simplifies deployment and failure isolation. For example, cloud services often use per-customer dedicated instances to meet security goals, then optimize them over time.
Hardware Environments
Section titled “Hardware Environments”The machine layer supports a variety of compute backends. Operators can run on bare-metal servers or virtual machines (VMs) with any operating system. It even supports lightweight microVMs (like AWS Firecracker) for fast, secure environments. Firecracker, for instance, lets the platform launch microVMs in milliseconds with strong isolation, combining the security of VMs with container-like efficiency. Robots or specialized devices (“be the robot” machines) can also plug in here, treating a physical robot as the machine for an Operator. Storage volumes (network-attached or block storage) can be attached to each machine for persistence, just as cloud VMs use attachable disks.
Isolation and Security
Section titled “Isolation and Security”Each Operator’s machine is strongly sandboxed. Hardware-level isolation (Trusted Execution Environments, or TEEs) can be used to protect sensitive code and data. A TEE is a secure enclave in the CPU that runs code in complete isolation from the main OS. For example, financial or healthcare systems use TEEs to process confidential data safely. In addition, the platform uses standard virtualization and container techniques for sandboxing. For instance, Linux containers use namespaces to give each Operator a confined view of the system (separate filesystem, processes, network, etc.). These layers ensure one Operator cannot interfere with another or the host, limiting damage in case of compromise.